Comprehensive protection for mobile devices
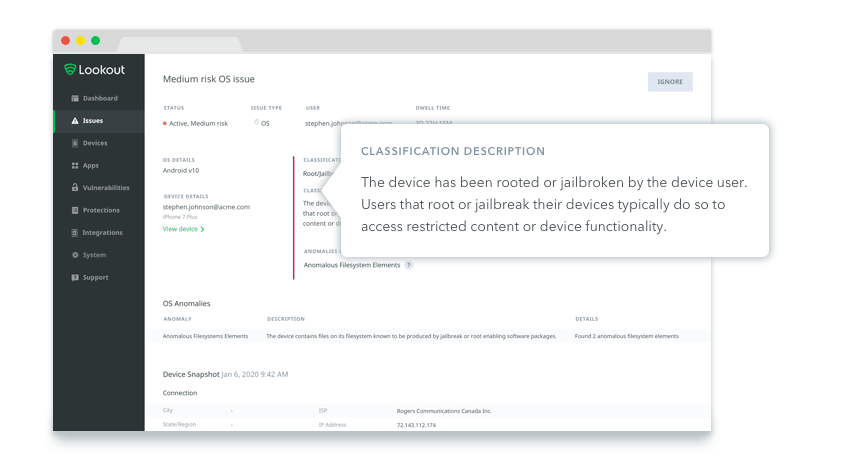
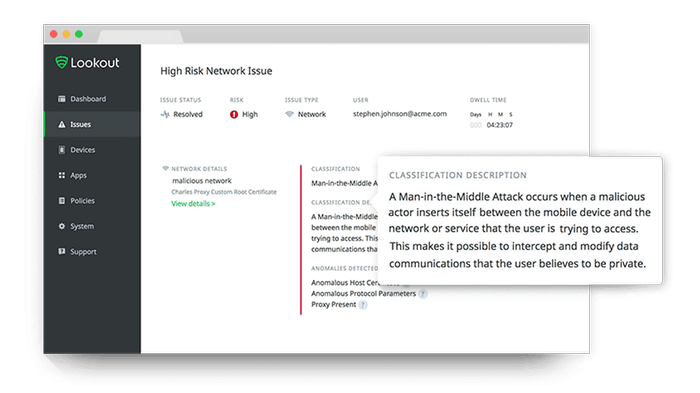
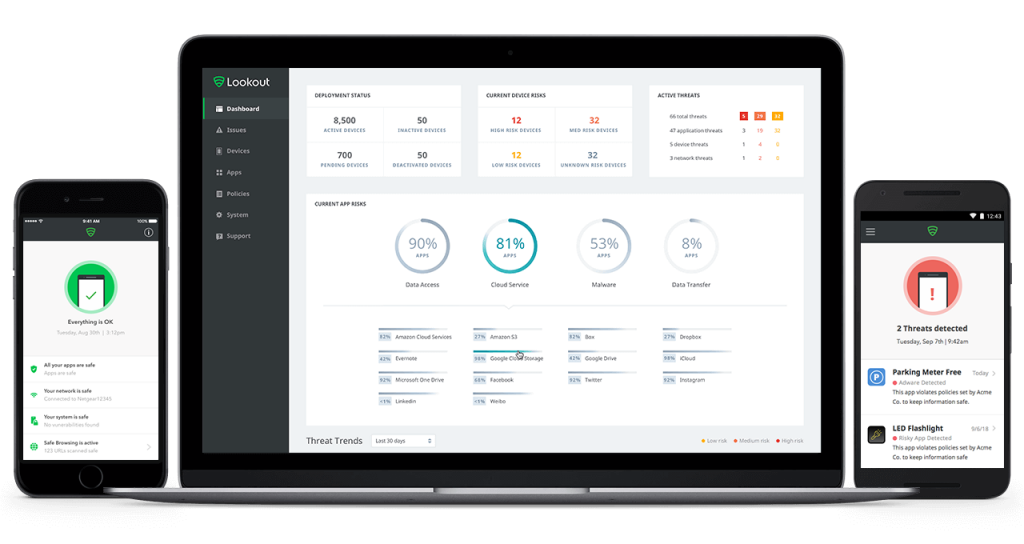
Lookout ensures a high level of security for endpoints, data, and applications. The solution allows only trusted devices to access corporate data and detects app-, device-, network- and web-based risks before they cause any damage. But there are a few things to keep in mind during implementation to take full advantage of its features.
We have many years of expertise for Lookout and can combine this with our experience in the enterprise mobility sector. Thanks to a good partnership, we can keep up with the rapid developments in the mobile security sector and always guarantee secure protection for your mobile devices. This way, you can protect sensitive data, avoid high economic damage and exploit the potential that mobile devices certainly offer.
Our services
Analysis and conception
We show you how to achieve effective data protection with Lookout and advise you on which countermeasures should be taken for which incidents. We can also help you add a security component to your company apps so that sensitive customer data is proactively protected.
Hosting in our data center
We can host Lookout in EBF's secure data center and provide it to you without a long implementation time.
Learn more about our hosting services
Licensing
We provide you with Lookout licenses quickly and easily – even for testing purposes.
Rollout
We thoroughly prepare the rollout of Lookout. This way, we ensure that the solution is implemented properly on all employee devices, where it provides effective protection.
Integration into a UEM system
Lookout can be integrated into various UEM systems and can be centrally distributed through them. This allows you to effectively protect your entire device pool.

- Support
Your benefits

- Increased security
- Effective defense against phishing attacks
- Individual consulting and support
- Close contact to the manufacturer
Contact Us
Contact us, if you have any questions. We will be happy to advise you and provide you with a customised quote.